Introduction
Advanced BitLocker Troubleshooting is crucial in the field of data security, and BitLocker, Microsoft's dedicated encryption tool, stands at the forefront for Windows users. With the Windows 11 security features, Microsoft enhances this protection, ensuring data safety even in today's complex digital landscape. While BitLocker is a key component in safeguarding information, understanding its use and troubleshooting is essential for users.
This article serves as a comprehensive guide for both troubleshooting BitLocker issues and implementing proactive measures to enhance data protection.
In this article, you will learn:
- Effective troubleshooting for BitLocker problems.
- Strategies to prevent BitLocker recovery prompts.
- Advanced BitLocker management on Windows.
As we delve into these topics, our aim is to equip you with the knowledge and tools necessary for seamless BitLocker operation, ensuring your data's security on your Windows device.


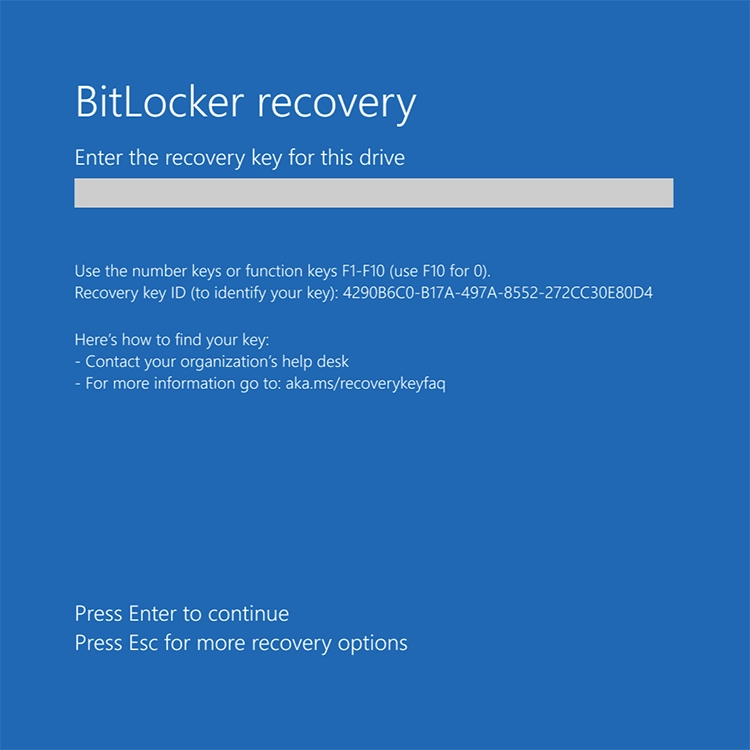
Encountering the BitLocker Recovery Screen
The BitLocker recovery screen serves as a crucial safety mechanism in Windows systems. It activates automatically when the system detects any significant changes or potential security threats. This feature, while vital for protecting your data, can be somewhat disconcerting, particularly for users who are not familiar with its purpose or functionality.
For an in-depth understanding of the BitLocker recovery process, especially for Surface devices, you can refer to our detailed post Solving BitLocker Recovery Key Prompt: A Step-by-Step Guide. However, to provide you with quick guidance in most situations, here is a concise version:
Why Does the Recovery Screen Appear?
Understanding why this screen appears is key to both maintaining your data's security and resolving any issues efficiently. Whether due to hardware modifications, firmware updates, or potential security breaches, this screen is BitLocker's way of ensuring that your encrypted data remains secure. Promptly addressing the cause of this alert and knowing how to respond to it is essential for a swift and effective resolution.
- Hardware Modifications: BitLocker is sensitive to changes in the hardware configuration. For instance, replacing the motherboard or altering BIOS settings can be perceived as potential security threats, prompting BitLocker to enter recovery mode.
- Firmware Updates: Similarly, updates to the BIOS or firmware are seen by BitLocker as changes that could compromise security, thus triggering the recovery screen.
- Potential Security Breaches: BitLocker is designed to detect any form of tampering or unusual changes to the system. It activates the recovery mode to protect encrypted data from perceived threats.
Resolving the BitLocker Recovery Prompt
Dealing with the BitLocker recovery screen might seem daunting, but with these systematic steps, you can regain control and secure your data effectively.
- Assess the Trigger: The first step in resolving the issue is to understand what triggered the recovery screen - hardware changes, firmware updates, or potential security threats.
- Recovery Key Utilization: At the initiation of BitLocker, a 48-digit recovery key is generated. This key is crucial for unlocking the drive in recovery scenarios.
- System Access Restoration: To regain access to the system, you need to enter the recovery key as prompted.
- BitLocker Reset: Once access is restored, it's recommended to reset BitLocker by suspending and then re-enabling encryption. This step acknowledges the changes and resets the security protocols.
- Update Recovery Key Backup: If there's a TPM reset, a new recovery key might be generated. It's important to securely back up this new key.
Preventive Insights
Incorporating these preventive measures can significantly reduce the chances of encountering the BitLocker recovery screen, ensuring smoother operation and enhanced security.
- Pre-Change Suspension: Before making significant hardware or firmware updates, suspending BitLocker can prevent the recovery screen from appearing.
- Regular Recovery Key Maintenance: Regularly backing up the BitLocker recovery key is vital. This ensures that you have access to it when needed and prevents data loss in case of emergencies.
Understanding the triggers for the BitLocker recovery screen and knowing how to respond to them is essential for maintaining the security of your data. Implementing preventive measures like suspending BitLocker before major changes and regularly backing up the recovery key can minimize disruptions and enhance overall security. This knowledge not only helps in effectively managing BitLocker encryption but also in maintaining seamless and secure operations of your Windows device.
Password Prompt Issues
Password prompt issues, including forgotten passwords and unresponsive input fields, are frequent stumbling blocks for BitLocker users. Effective management of these challenges is key to ensuring uninterrupted access to encrypted data. In this section of Advanced BitLocker Troubleshooting, we delve into strategies and solutions that address these specific password-related hurdles, providing users with the necessary insights and techniques to maintain secure and accessible encrypted data.
Typical Password Prompt Problems
Understanding common password prompt problems helps in developing strategies for quick and efficient resolution.
- Forgotten Passwords: Often, users forget their password, especially if it's infrequently used or seldom accessed.
- Unresponsive Input Fields: Users might encounter unresponsive password input fields, potentially due to software glitches or compatibility issues, especially in pre-boot situations.
Password Reset and Recovery Solutions
Navigating password reset and recovery involves several key steps, ensuring access is maintained even in challenging situations.
- Utilizing the Recovery Key: The primary solution for a forgotten password is the 48-digit BitLocker recovery key, generated during initial setup and ideally stored securely.
- Password Reset in Windows: After using the recovery key to unlock the drive and access Windows, reset the password via the Users management tool in the Control Panel.
- The Necessity of the Recovery Key: Without the recovery key, password resetting might be impossible, highlighting the need for secure storage of this key.
TPM's Role in Password Management
The Trusted Platform Module (TPM) plays a significant role in enhancing BitLocker's password management capabilities.
- Enhanced Security with TPM: Devices equipped with TPM provide an additional layer of security, as TPM stores encryption keys beyond just the password.
- TPM-Assisted Password Recovery: In systems with a TPM, recovering access through the BitLocker recovery key can be more streamlined, with TPM aiding in system authentication.
Proactive Password Management Strategies
Implementing preventive measures can significantly reduce the occurrence of password-related issues.
- Routine Password Updates and Testing: Regularly updating and testing passwords helps prevent forgetting them.
- Secure Recovery Key Backup: Always maintain a backup of your BitLocker recovery key in a secure location, separate from your device.
Effectively managing BitLocker password prompts and understanding the role of TPM is crucial in ensuring seamless access to encrypted data on Windows devices.
Inaccessible Recovery Key
The recovery key is a pivotal element of BitLocker encryption, acting as a failsafe for your encrypted data. Yet, situations may arise where this key becomes lost or inaccessible, and knowing how to navigate these instances is vital for continuous data protection.
Common Causes of Key Inaccessibility
Recognizing scenarios that lead to an inaccessible recovery key helps in preemptive action and recovery planning.
- Misplaced or Forgotten Key: The most typical issue is misplacing or forgetting the recovery key's storage location, often due to inadequate backup or changes in storage methods.
- User Account or Service Changes: For digitally stored keys, alterations in user accounts or cloud services can render the key unreachable, possibly from account closures or lost credentials.
- Device or System Failures: Key loss can also result from failures or corruption of the device or system where the key was stored.
Key Recovery Tactics
Here are strategies to retrieve a lost or inaccessible BitLocker recovery key.
- Microsoft Account Check: Personal device users often save their BitLocker key to their Microsoft account. Accessing this account online may reveal the stored key.
- Active Directory Lookup (Enterprise Users): In corporate settings, BitLocker keys are typically backed up to Active Directory, retrievable by IT admins.
- Utilizing Backup Keys: A backup of the recovery key, stored securely and separately, is a reliable recovery method.
- Identifying Recovery Key: Each key has a unique identifier, useful in locating the correct key from backups when prompted.
Proactive Key Management Measures
Adopting preventive measures can significantly reduce the risk of key inaccessibility.
- Routine Key Backups: Consistently back up your BitLocker keys in various secure locations, both physical and digital, separate from the encrypted drive.
- Key Documentation: Record pertinent details alongside the recovery key, such as generation date, associated device, and unique identifiers.
Understanding and applying these strategies is crucial in scenarios where the BitLocker recovery key is inaccessible, ensuring your encrypted data remains protected and retrievable.
BitLocker Drive Encryption Errors
Encountering errors during the BitLocker encryption process can be a challenging experience. These errors may occur at various stages, such as during the initial setup, drive preparation, or even in routine usage. To ensure a smooth experience with BitLocker, it's crucial to understand these errors comprehensively. This involves not only recognizing the types of errors that can occur but also applying advanced troubleshooting techniques to effectively resolve them.
Typical Encryption Process Errors
Understanding common encryption errors is the foundational step towards effective troubleshooting and prevention.
- Failed Encryption Processes:
- Causes: These failures can be attributed to various issues like disk errors, insufficient disk space, or conflicts with other software.
- Impact: Such failures can halt the encryption process, leaving data unprotected and potentially leading to data integrity issues.
- Errors in Drive Preparation:
- Importance: Proper drive preparation is a prerequisite for BitLocker. This includes creating and formatting partitions in a specific way.
- Consequences: Errors in these preparatory steps can prevent BitLocker from initializing or functioning correctly.
Effective Solutions for Encryption Errors
Strategically resolving these errors can prevent them from occurring or recurring.
- Disk Integrity Checks:
- Tool Usage: Utilize tools like 'chkdsk' to inspect and fix disk errors. This step should be done before initiating BitLocker encryption.
- Purpose: This ensures the drive is in good health and free from errors that could disrupt the encryption process.
- Ensuring Adequate Disk Space:
- Requirement: Confirm there's enough free space on the drive for the encryption process, including the necessary metadata.
- Action: Free up space or use a drive with sufficient capacity.
- TPM Configuration Verification:
- Role of TPM: The Trusted Platform Module (TPM) is integral for storing encryption keys and managing BitLocker.
- Check: Ensure that the TPM is enabled, operational, and properly configured.
- Retry Encryption After Issue Resolution:
- Approach: Once issues are identified and resolved, attempt to encrypt the drive again, making sure all prerequisites are met.
- Conflict Resolution:
- Software Conflicts: Identify and address conflicts with other software, especially other disk utilities or encryption tools.
- Resolution: This might involve disabling or uninstalling conflicting software.
Preventive Strategies for Encryption Stability
Employing preventive measures regularly can greatly reduce the likelihood of encountering encryption errors.
- Routine System Maintenance:
- Practice: Regular checks for system and disk health can preempt many causes of encryption errors.
- Benefit: This proactive approach helps maintain system stability and readiness for encryption.
- Data Backup Prior to Encryption:
- Precaution: Always ensure that critical data is backed up before starting the BitLocker encryption process.
- Reason: This safeguards against data loss in the event of unexpected errors during the encryption process.
Being well-informed about BitLocker drive encryption errors and their solutions is pivotal for a successful and hassle-free encryption process. Understanding the nature of these errors, along with implementing both reactive solutions and proactive strategies, is key to effectively securing your data with BitLocker. This comprehensive approach not only resolves existing issues but also minimizes the risk of future problems, ensuring a robust and reliable data protection environment.
BitLocker Encryption and Removable Data Drives
BitLocker's capability to encrypt removable data drives, including USB flash drives and external hard drives, is a significant extension of its security functionality. This feature is especially valuable for protecting sensitive data on portable devices. However, the use of BitLocker with these removable drives often brings unique challenges that differ from those encountered with internal drives. Understanding these challenges is key to ensuring both the security and accessibility of the data on these devices.
Common Challenges with Removable Drives
Recognizing and understanding common issues with BitLocker-encrypted removable drives is crucial.
- Unlocking Difficulties:
- Causes: Users may face challenges unlocking drives due to reasons like forgotten passwords, misplaced or lost smart cards, or even due to data corruption within the drive.
- Impact: These issues can prevent access to vital data stored on the drives.
- Inaccessible Drive Contents:
- Problem: Sometimes, even after successful unlocking, the contents of the drives may appear inaccessible or unreadable.
- Reasons: This is often the result of file system errors or physical drive corruption.
Resolving Removable Drive Issues
Effective strategies and solutions are essential to address and resolve these issues.
- Compatibility Checks:
- Action: Ensure the removable drive is compatible with BitLocker's requirements, especially for older or less sophisticated models.
- Purpose: Compatibility issues can lead to encryption and accessibility problems.
- Password and Smart Card Management:
- Key Point: Proper management and use of passwords and smart cards are critical. Verify their functionality and ensure they are used correctly.
- Reminder: Regularly check that these security components are operational and accessible.
- Connection Troubleshooting:
- Method: If unlocking issues persist, experiment with different USB ports or another computer to isolate the issue.
- Goal: Determine whether the problem is with the drive itself or the connection/interface.
- Drive Recovery Steps:
- Solution: Use a backed-up BitLocker recovery key for drives where the regular unlocking mechanism fails.
- Importance: This is often the last resort to regain access to encrypted data.
- Using Disk Repair Tools:
- Tool: Employ disk repair tools like 'chkdsk' for drives that are unlocked but still show inaccessible data.
- Caution: Proceed carefully with these tools to avoid further data loss.
Proactive Strategies for Drive Protection
Implementing preventive measures enhances the security and reliability of removable drives.
- Consistent Data Backups:
- Recommendation: Regularly back up the data stored on removable drives to prevent data loss.
- Benefit: This ensures that critical data is not lost in case of encryption or access issues.
- Secured Passwords and Key Storage:
- Practice: Store passwords, smart cards, and recovery keys securely and separately from the drives they protect.
- Reason: This minimizes the risk of losing access to encrypted drives due to lost or compromised security elements.
Effectively handling the specific challenges associated with using BitLocker on removable data drives is pivotal for maintaining the security and accessibility of your data. By understanding these challenges, applying targeted solutions, and adopting preventive measures, you can ensure that your data remains protected and accessible on these portable storage devices. This balanced approach to security and practicality makes BitLocker an invaluable tool for safeguarding data on removable drives.
Advanced BitLocker Troubleshooting Techniques: A Deep Dive
When tackling intricate BitLocker issues, standard troubleshooting methods may not always be adequate. This necessitates the use of advanced techniques, employing specialized tools and commands to accurately diagnose and effectively resolve complex problems. In the following section on Advanced BitLocker Troubleshooting Techniques, we will explore the use of the BitLocker Repair Tool, the management of BitLocker through Group Policy, and the utilization of PowerShell for advanced diagnostics and solutions, providing you with the necessary skills to handle even the most challenging BitLocker scenarios.


Using the BitLocker Repair Tool (Repair-bde)
The BitLocker Repair Tool, or Repair-bde, is an invaluable utility for recovering data from corrupted or damaged disks encrypted with BitLocker.
- Functionality: This tool is crucial for recovering data from encrypted volumes that have been corrupted or damaged. It works by extracting data from a BitLocker-encrypted disk and transferring it to a new, unencrypted drive.
- Requirements: To use the BitLocker Repair Tool, access to either the BitLocker recovery key or the password for the encrypted volume is essential.
Managing BitLocker with Group Policy
Group Policy offers comprehensive settings for BitLocker management, especially beneficial in enterprise environments. With Microsoft's expansion of BitLocker management capabilities for the enterprise, handling these complexities becomes more streamlined, offering robust solutions for modern enterprises.
- Range of Settings: Group Policy provides a wide array of settings for BitLocker management. This is particularly useful in enterprise environments where uniform encryption policies are essential.Key Applications: Through Group Policy, administrators can configure settings such as pre-boot recovery options, TPM (Trusted Platform Module) management, and automated unlocking processes for both fixed and removable drives
Leveraging PowerShell for BitLocker Management
PowerShell extends greater flexibility in managing BitLocker than the standard Control Panel interface.
- Command Suite: PowerShell offers a more flexible and comprehensive suite of commands for managing BitLocker compared to the standard Control Panel interface. These commands include enabling or disabling BitLocker, changing passwords, and exporting recovery keys.
- Diagnostic Capabilities: PowerShell is also a powerful tool for diagnosing BitLocker issues. Commands like
Get-BitLockerVolumeprovide detailed information about the status and configuration of BitLocker on a drive.
Proactive BitLocker Management
Adopting a proactive stance in managing BitLocker settings and familiarizing oneself with these advanced tools is crucial.
- Regular Policy Reviews: Consistently updating and reviewing Group Policy settings related to BitLocker ensures alignment with the latest organizational security policies and requirements.
- Familiarization with Tools: Being well-acquainted with tools like the BitLocker Repair Tool and PowerShell commands equips you with the necessary skills to handle complex BitLocker challenges.
Mastering these advanced BitLocker troubleshooting techniques is imperative for effectively addressing sophisticated BitLocker challenges. These methods ensure the integrity and security of encrypted data, providing a robust framework for data protection in various scenarios, from individual use to large-scale enterprise environments. By being proactive and well-versed in these advanced troubleshooting techniques, you can ensure that BitLocker continues to serve as a reliable and secure encryption solution.
Handling BitLocker in a Multi-Boot Environment
Managing BitLocker in a multi-boot environment, where multiple operating systems (OS) are installed on the same device, introduces unique challenges. This environment is particularly complex due to the varied interactions between different operating systems and BitLocker encryption. In this section, we explore advanced scenarios in multi-boot environments, focusing specifically on BitLocker troubleshooting. You'll gain insights into resolving common yet intricate issues, which is essential for maintaining the security and efficiency of your system.


Complexities in Multi-Boot Systems
The intricacies of multi-boot systems require careful consideration for effective BitLocker management:
- Varied Encryption States:
- Challenge: Different operating systems might have varying encryption requirements or statuses, leading to potential inconsistencies.
- Impact: This can cause complications in how BitLocker is applied or accessed across different systems.
- Boot Loader Dynamics:
- Issue: BitLocker's interaction with the boot loader is crucial. Alterations made to the boot configuration by one operating system can unintentionally trigger BitLocker recovery mode in others, especially if they share the same physical drive.
Effective BitLocker Management Strategies
To manage BitLocker effectively in a multi-boot environment, consider the following strategies:
- Separate Drives for Each OS:
- Approach: Installing different operating systems on separate physical drives can reduce the risk of conflicts and simplify encryption management.
- Benefit: This minimizes the interaction between different OS boot loaders and BitLocker.
- Uniform Encryption Across Systems:
- Strategy: In scenarios where operating systems share a drive, aim for consistent encryption practices, like enabling BitLocker for all Windows installations.
- Reason: Consistency helps in managing recovery keys and encryption statuses more efficiently.
- Mindful Boot Order Adjustments:
- Caution: Be careful when altering the boot order or updating firmware, as these changes can activate BitLocker's security mechanisms.
- Recommendation: Always check the impact of such changes on BitLocker.
- Accessible Recovery Keys:
- Necessity: Keep BitLocker recovery keys readily available, especially important in multi-boot systems due to the increased likelihood of recovery prompts.
- Preparation: Ensure that you have access to the appropriate recovery keys for each OS.
- Consistent Data Backups:
- Practice: Regularly back up data across all operating systems to protect against potential BitLocker decryption or restoration needs.
- Security: This is a critical practice to safeguard your data in complex configurations.
Proactive Multi-Boot System Management
Implementing preventive measures can enhance the stability and security of multi-boot systems:
- Routine System Reviews:
- Action: Conduct regular checks of BitLocker status and boot configuration health for each operating system.
- Purpose: This helps identify potential issues early and allows for timely intervention.
- Detailed Documentation and Monitoring:
- Documentation: Keep thorough records of your multi-boot configuration, including details of encrypted partitions and their respective recovery keys.
- Monitoring: Track changes in boot processes and BitLocker statuses, particularly after system updates or modifications.
Effectively managing BitLocker in a multi-boot environment requires a deep understanding of its interactions with different operating systems and
boot configurations. By employing strategic approaches, such as using separate drives for each OS, maintaining uniform encryption practices, and being cautious with boot order adjustments, you can significantly mitigate BitLocker-related issues. Additionally, ensuring the accessibility of recovery keys and consistent data backups are paramount in these environments.
Proactive management, including regular system reviews and detailed documentation, further enhances the security and stability of multi-boot systems. By embracing these practices, you can create a secure and harmonious multi-boot environment, safeguarding your data across all installed operating systems. This comprehensive approach to BitLocker management in complex configurations is key to maintaining robust data protection and operational efficiency.
FAQs: Addressing Common Concerns and Queries
Here are some frequently asked questions about BitLocker issues on Windows devices, providing quick and concise answers to common concerns.
Common triggers include hardware changes and software updates. Address them by entering the recovery key and checking system integrity.
Yes, BitLocker can encrypt external hard drives and USB flash drives using BitLocker To Go, providing similar protection as it does for internal drives.
BitLocker encryption may slightly impact system performance, but for most users, this impact is negligible, especially on modern hardware.
To disable BitLocker, go to the Control Panel, select "System and Security," then "BitLocker Drive Encryption," and choose "Turn off BitLocker." This process will decrypt your drive.
Data recovery from a corrupted BitLocker-encrypted drive is possible using the BitLocker Repair Tool, but you'll need the recovery key. Note that success is not guaranteed and depends on the extent of the corruption.
BitLocker is available in Windows Vista, 7 (Enterprise and Ultimate), 8, 8.1, 10 (Pro, Enterprise, and Education), and Windows 11. It's not available in Home editions of Windows.
Without the key, recovery is highly improbable. Maintain multiple backups of your recovery key.
Suspending BitLocker leaves data temporarily unencrypted. It’s useful for system updates but should be re-enabled promptly.
Conclusion
In this comprehensive exploration of BitLocker for Windows devices, we have navigated through the intricacies of BitLocker encryption, offering insights into troubleshooting common issues and implementing effective preventive measures. Our journey has equipped you with the knowledge to tackle BitLocker challenges confidently, ensuring your data remains secure yet accessible.
The Path to Proactive Protection: Encouraging proactive measures is key. Regularly updating and testing BitLocker configurations, backing up recovery keys, and staying informed about system changes are pivotal practices. These steps not only secure your data but also ensure a smooth, uninterrupted experience with your Windows device.
Expert Assistance at Your Fingertips: For situations that require a more expert touch, remember that professional help is just a click away. At FixYourSurface.com, we specialize in addressing a wide range of issues related to Surface and Windows devices. Our expertise extends to guiding you through the most complex BitLocker challenges, ensuring your device's security is uncompromised.
In conclusion, while BitLocker is a powerful tool for data protection, its effectiveness is maximized when managed with knowledge and care. Stay vigilant, stay prepared, and for any complexities beyond your scope, our experts at FixYourSurface.com are here to assist you.